
API Security Best Practices for 2026: Gateway/WAAP, OAuth 2.1, Workload Identity & CI/CD Recipes
Secure APIs in 2026 with gateway/WAAP, OAuth 2.1 + DPoP/mTLS, workload identities, schema validation, and CI/CD gates—plus ready-to-paste playbooks....
API Attacks: Real-World Examples, OWASP Risks & Prevention
Learn the most common API attacks, real-world breach examples, OWASP Top 10 risks, and practical defenses to secure APIs end-to-end....

API Security 101: Foundations, Threats & Best Practices
Learn API security fundamentals: OWASP Top 10, CI/CD integration, GraphQL/gRPC, and real breach lessons to secure your APIs from day...

API Security Checklist: 12 Steps to a Secure API
Secure your APIs with this comprehensive 12-step checklist, covering authentication, data protection, monitoring, and more....

API Security Checklist 2025: 12 Steps Every Developer Needs
Follow this 12-step API security checklist (2025 edition) with threat modeling, real examples, PDF, and best practices for robust API...
API Security Trends
API security is critical as breaches rise, with advanced threats emerging. Learn about trends, risks, and strategies to safeguard your...
Common API Security Vulnerabilities & Solutions (2025 Guide)
Learn the top API vulnerabilities like BOLA, mass assignment, GraphQL abuse, and JWT misuse. See practical solutions, OWASP Top 10...

Top 10 Cybersecurity Challenges Facing FinTech in 2025
Explore the critical cybersecurity challenges FinTech companies face in 2025, including data breaches, insider threats, and AI-driven attacks....
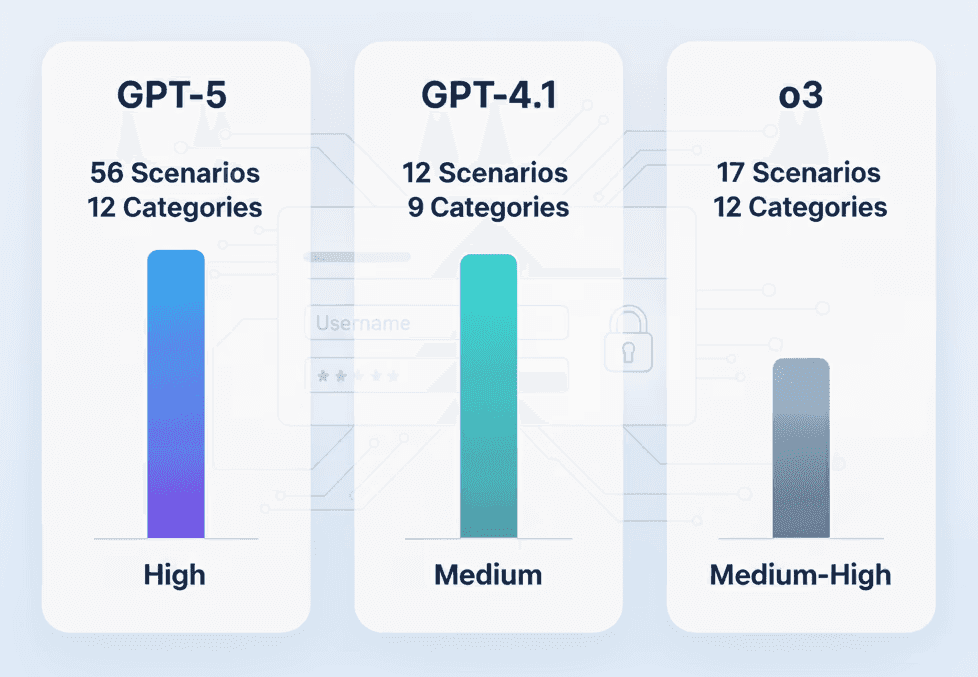
GPT-5 vs O3 vs GPT-4.1, Which one is better for Penetration Testing
Compare GPT-5, O3, and GPT-4.1 for penetration testing. Discover which AI model delivers the best results for ethical hacking....
How to Get a Rugcheck API Key and Start Using the API
Learn how to secure your tokens from scams using a powerful API that automates risk detection and enhances application security....

OWASP API Top 10 (2023): Complete Guide with Tests & Fixes
Learn the OWASP API Top 10 (2023): BOLA, BOPLA, SSRF & more. Includes real exploits, CI/CD checks, GraphQL/gRPC notes, and...

Rapid7 Not Enough? Try These 10 Cutting-Edge Cybersecurity Alternatives
Explore top alternatives to enhance your cybersecurity and threat detection strategies in 2025, tailored for diverse organizational needs....

Security Testing Tools and its Types
Explore essential security testing tools and their types, including SAST, DAST, and IAST, to protect your software from vulnerabilities....
SQL Injection (SQLi): Types, Examples & Prevention
Learn SQL injection types (error, UNION, blind, OOB) with examples—and prevent SQLi using parameterized queries, DB least-privilege, WAF rules, and...

Top 10 DAST Tools for 2025
Explore the top DAST tools of 2025 for effective API security testing, integration, and automation in modern development workflows...

What Is DevSecOps? Definition and 10 Best Practices
Learn what DevSecOps is and how to implement it—definition, core principles, and best practices: threat modeling, IaC guardrails, SBOMs, policy-as-code....

Top 12 Vulnerability Scanning Tools
Explore the top vulnerability scanning tools essential for identifying and mitigating security risks in software, networks, and systems....
Top API Security Vendors: Compare Features & Services
Explore the leading API security vendors, comparing their features, strengths, and weaknesses to enhance your organization's API protection strategy....
Top API Security Vulnerabilities (2025) & How to Prevent Them
Discover the top API vulnerabilities like BOLA, mass assignment, and SSRF. Includes real breaches, fixes, and CI/CD security practices....
What Is OAuth 2.0 and How Does It Work?
Explore OAuth 2.0, a secure framework for app access to user data, ensuring privacy through token-based permissions and limited scopes....

What Is OAuth 2.0 (and OAuth 2.1)? Flows, PKCE, OIDC & Best Practices
Learn OAuth 2.0 essentials—Authorization Code with PKCE, Client Credentials, Device Code—plus OAuth 2.1 updates, OIDC, scopes, token safety, and CI/CD...

What is OpenID Connect?
Unlock the power of OpenID Connect! Learn how OIDC simplifies online logins, enhances security, and provides seamless user experiences....
What Is Penetration Testing? Types, Methodologies, Compliance & CI/CD (2025 Guide)
Learn pen testing basics and beyond: types (web, API, cloud), PTES/NIST/OWASP methods, PCI-DSS ties, tools (Kali, Nmap, Metasploit), frequency, scope...
Why You Need an API Inventory — +10 Practical Steps to Build and Maintain It
Discover why a complete API inventory is critical for security, compliance, and efficiency — and follow our 10 actionable steps...